Connect to on-prem Active Directory
- Prerequisites
- Users and permissions for connecting to on-prem Active Directory
- Communication ports and firewall configuration
- Setting up the target system connector
Prerequisites
In order to connect an IAM.cloud instance to an on-prem Active Directory, the IAM.cloud on-prem Gateway has to deployed in the customers on-prem network.
Detailed information about the installation of the IAM.cloud on-prem Gateway can be found here:
Installation of the IAM.cloud on-prem gateway
Users and permissions for connecting to on-prem Active Directory
To connect to an on-prem Active Directory, a user must be provided with the following authorizations:
Member of the Active Directory group “Domain administrators”
In case of a hierarchical domain structure, the user must be member of the Active Directory group “Enterprise Admins”.
In case the necessary permissions can not be provided due to compliance concerns, IAM.cloud supports the following, fine-grained permissions that have to be provided to the user account:
Permissions on the connection base object and all objects below
Read
Write
Create all child objects
Delete all child objects
Read permissions
Write permissions
Modify owner
Read All Properties
Write All Properties
All Extended Rights
DeleteSubTree
As essential permissions are based upon DACLs of Active Directory objects, this requires permissions to change the DACL of Active Directory objects as well. This will be allowed in the following cases:
The user account applying the change to the DACL is owner of the object.
The user account applying the change to the DACL is member of the same primary group as the object owner. This is usually the Domain administrators group.
It’s not recommended to take the ownership of objects using the target system connector user account. Instead, we recommend using the Domain administrators group as primary group for the target system connector user account.
Communication ports and firewall configuration
Hint: This section does only apply, if the IAM.cloud on prem connector resides in a highly secure network and network connections within the customers on-prem network are secured using internal firewalls.
The IAM.cloud on-prem Active Directory connector requires the following network ports:
Port | Description |
|---|---|
88 | Kerberos authentication system |
135 | Microsoft End Point Mapper and DCE / RPC Locator Server |
137 | NetBIOS Name Service |
139 | NetBIOS Session Service |
389 | LDAP port (no SSL) |
445 | Microsoft-DS Active Directory, Windows shares |
53 | Domain Name System (DNS) |
636 | LDAP port (SSL) |
3268 | Global catalog, required for searching the global catalog |
3269 | Global catalog, required for searching the global catalog |
Setting up the target system connector
To connect to an on-prem Active Directory connect to the IAM.cloud with a user having the IAM.cloud application role “Global Target system configurator”. Click “Responsibilities” and “Target systems”.
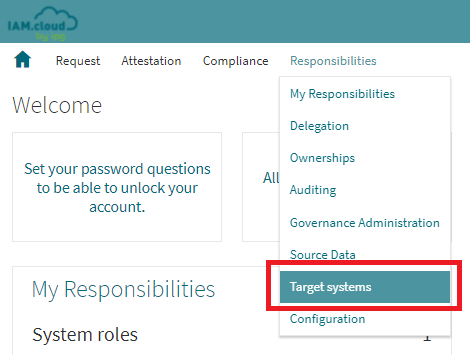
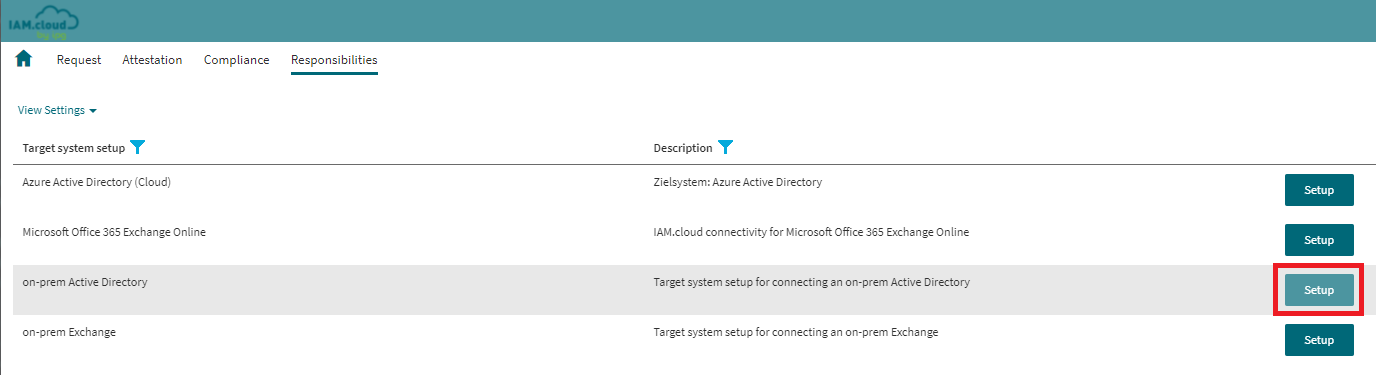
In the list of available target system connectors select the connector “on-prem Active Directory“ and click the button “Setup” to create a new target system instance.
Name the target system instance, put in a description and select the IAM.cloud on-prem Gateway as the execution server.
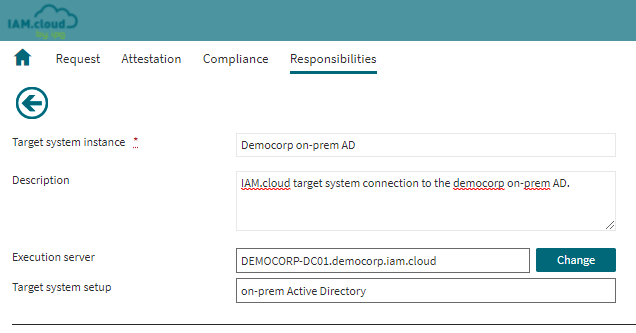
| Attribute | Description |
|---|---|
| Target system instance | The name of the target system instance - this is a freetext value with no technical relevance and will be used as the display name for the target system instance only. |
Description | The description to the target system instance - this is a freetext value with no technical relevance and will be used for documentation purposes only. |
| Execution server | The server that will be executing the target system connectivity tasks. This has to be an IAM.cloud on-prem Gateway in order to connect to the on-prem Active Directory from within the on-prem network. |
After entering the target system instance attributes, click “Save” to enable the technical configuration of the target system connector.
Fill in the technical attributes for the target system connector and click “Save”
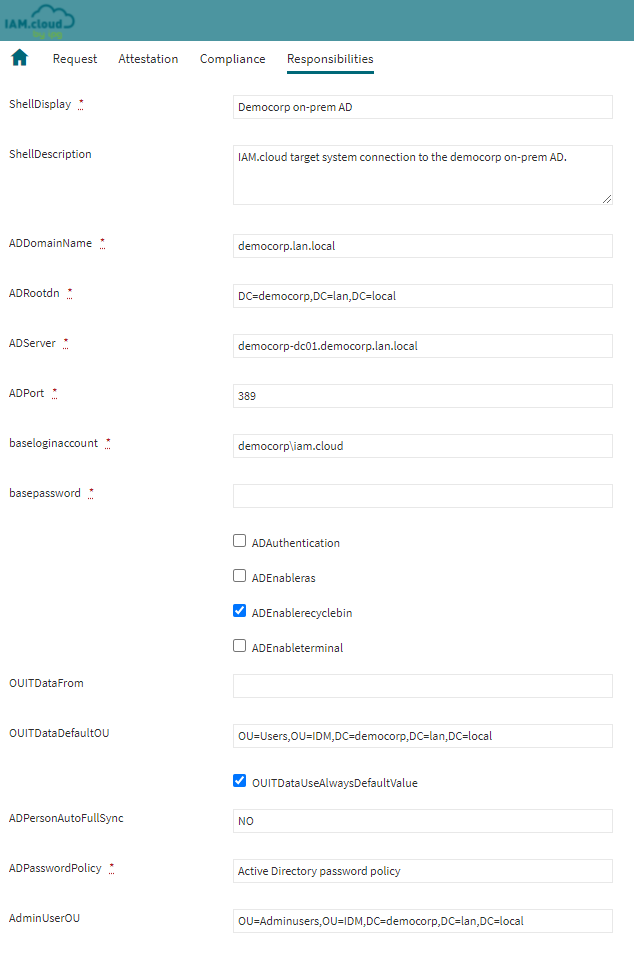
Attribute | Description |
|---|---|
ShellDisplay | The value in the attribute ShellDisplay will be used as the name of the technical connectivity setup. |
ShellDescription | The value in the attribute ShellDescription will be used for documentation purposes for the technical connectivity setup. |
ADDomainName | The ADDomainName attribute represents the full qualified domain name (FQDN) of the on-prem Active Directory domain that will be connected. |
ADRootDN | The ADRootDN attribute represents the Distinguished Name attribute of the on-prem Active Directory domain that will be connected. |
ADServer | The ADServer attribute represents the full qualified domain name of the domain controller that will be leveraged to connect the on-prem Active Directory. |
ADPort | The ADPort attribute represents the LDAP port to be used to connect the on-prem Active Directory. Usually this will be:
|
baseloginaccount | The baseloginaccount represents the technical user account being used to connect to the on-prem Active Directory. The user name can be given in the following notation options:
|
basepassword | The basepassword is the password of the technical user account being used to connect to the on-prem Active Directory. |
ADAuthentication | The ADauthentication attribute represents the configuration option if AD native authentication should be used to connect to the on-prem Active Directory. Usually this options is not necessary. |
ADenableRAS | The ADenableRAS attribute represents the configuration option if RAS (Remote Access Services) attributes of AD objects will be managed by IAM.cloud. |
ADenableRecycleBin | The ADenableRecycleBin attribute represents the configuration option if the recycle bin feature is activated in the on-prem Active Directory domain. |
ADenableTerminal | The ADenableTerminal attribute represents the configuration option if terminal attributes will be managed by IAM.cloud. |
OUITDataFrom | The OUITDataFrom attribute represents a configuration option from which entity the IT operation data will be pulled. Valid options are:
|
OUITDataDefaultOU | The OUITDataDefaultOU attribute represents the distinguished name of the default OU to provision regular users to in case there is not OU configured within the IT operation data or all users will be provisioned to one single OU by default. |
OUITDataUseAlwaysDefault | The configuration option defines if all users are provisioned to the default OU named in OUITDataDefaultOU by default or not. |
ADPersonAutoFullSync | This configuration will be used to decide wether identities will be automatically assigned to user accounts from the on-prem Active Directory during the regular reconciliation between IAM.cloud and the on-prem Active Directory domain. The following values are possible:
|
ADPasswordPolicy | This attributes represents the password policy that will be applied while creating new user accounts by IAM.cloud. The default password policy is called “Active Directory password policy”. If customers wish to leverage customer specific password policies, reach out to your IPG account representative or open a service request. |
AdminUserOU | The OUITDataDefaultOU attribute represents the distinguished name of the default OU to provision admin-users to in case there is not OU configured within the IT operation data or all users will be provisioned to one single OU by default. |
If all mandatory attribute values are filled in and the configuration is saved, the button “Rollout” will be enabled. Click “Rollout” to connect the on-prem Active Directory to IAM.cloud.
Related articles
-
Page:
-
Page:
-
Page:
-
Page:
-
Page: