Connect to Azure Active Directory
- Prerequisites
- Users and permissions for connecting to Azure Active Directory
- Integrating IAM.cloud as enterprise application
- Setting up the target system connector
Prerequisites
No special prerequisites have to be in place.
Users and permissions for connecting to Azure Active Directory
To connect to Azure Active Directory, a technical user must be provided in Azure active Directory with the following authorizations:
Member in the global administrator administrator organization role
Integrating IAM.cloud as enterprise application
Before connecting IAM.cloud to Azure active Directory, IAM.cloud has to be configured as an enterprise application in Azure Active Directory. That for, log into the Microsoft Azure Admin Portal: Azure Admin Portal
Switch to the Azure Active Directory admin center.
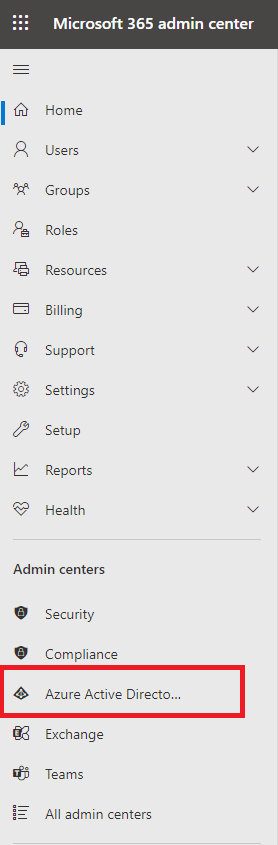
In the Microsoft Azure Active Directory admin center, create a new enterprise application for your directory.
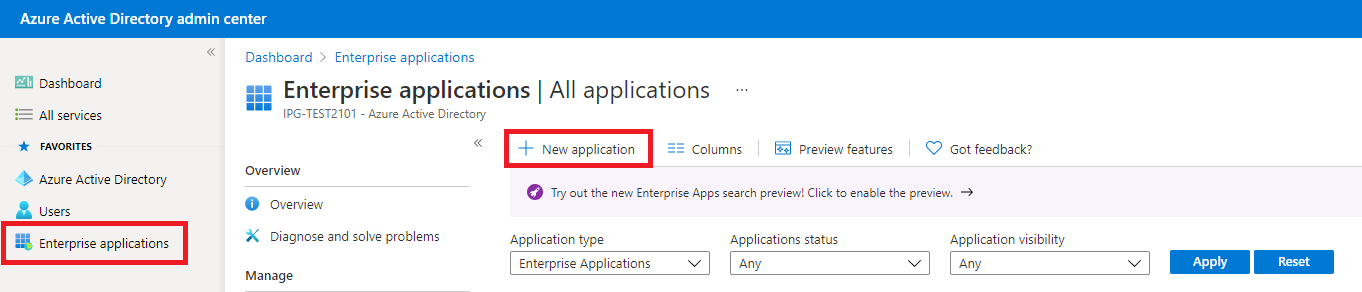
Click “Create your own application”

While naming the enterprise application, select the option “Register an application to integrate with Azure AD (App you’re developing)”. Then click “Create”.
IPG recommends to limit the access to the API to “Accounts in this organizational directory only” (Single tenant). Then click “Register”. Then switch to the Azure Active Directory dashboard and click “App registrations”.
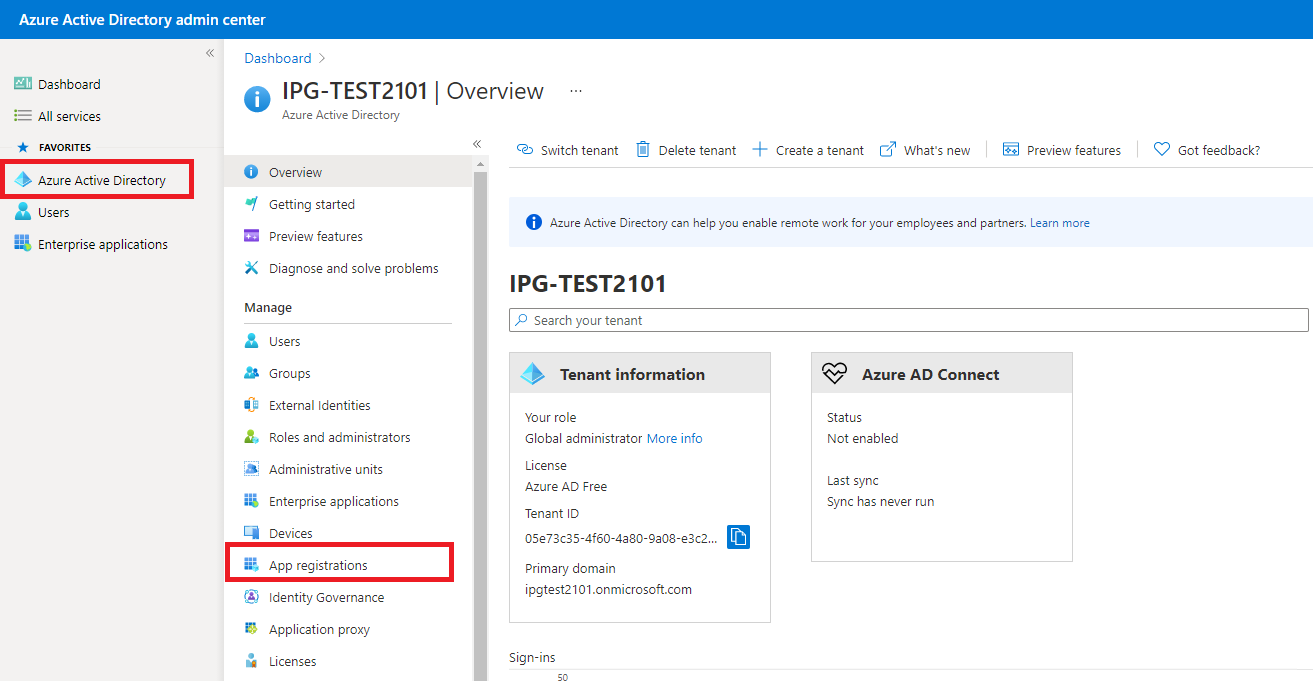
Hint: While setting up the application, an application ID (client ID) is created. This application ID is required for setting up the target system connector.
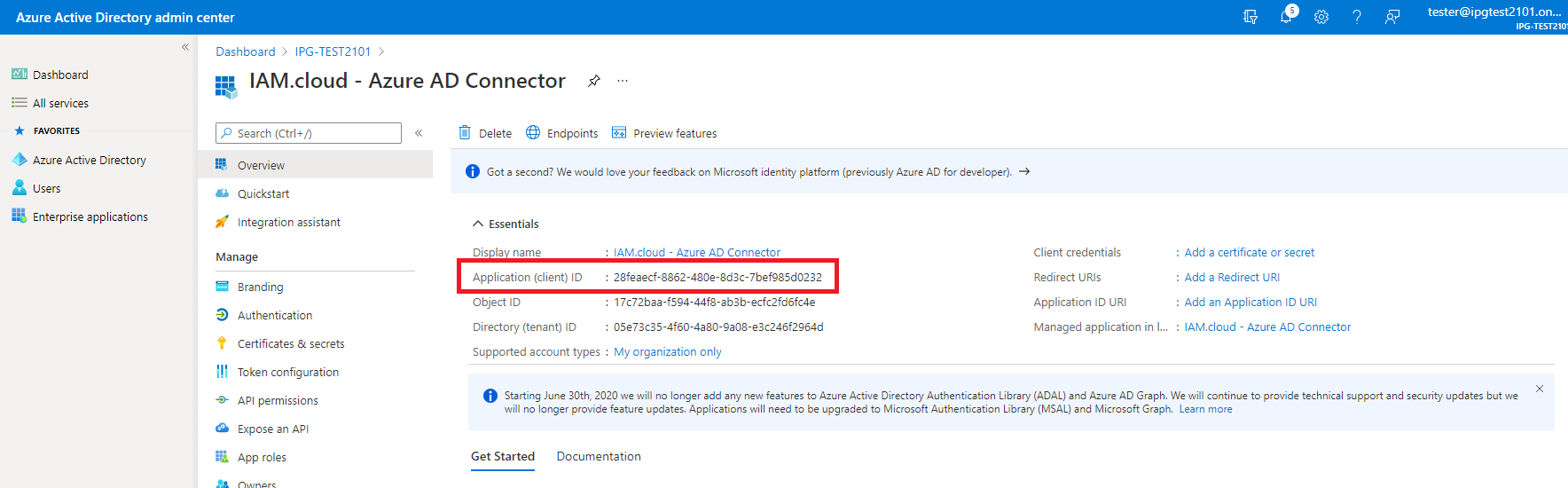
Select the newly created application from the list of applications and click “API permissions”.
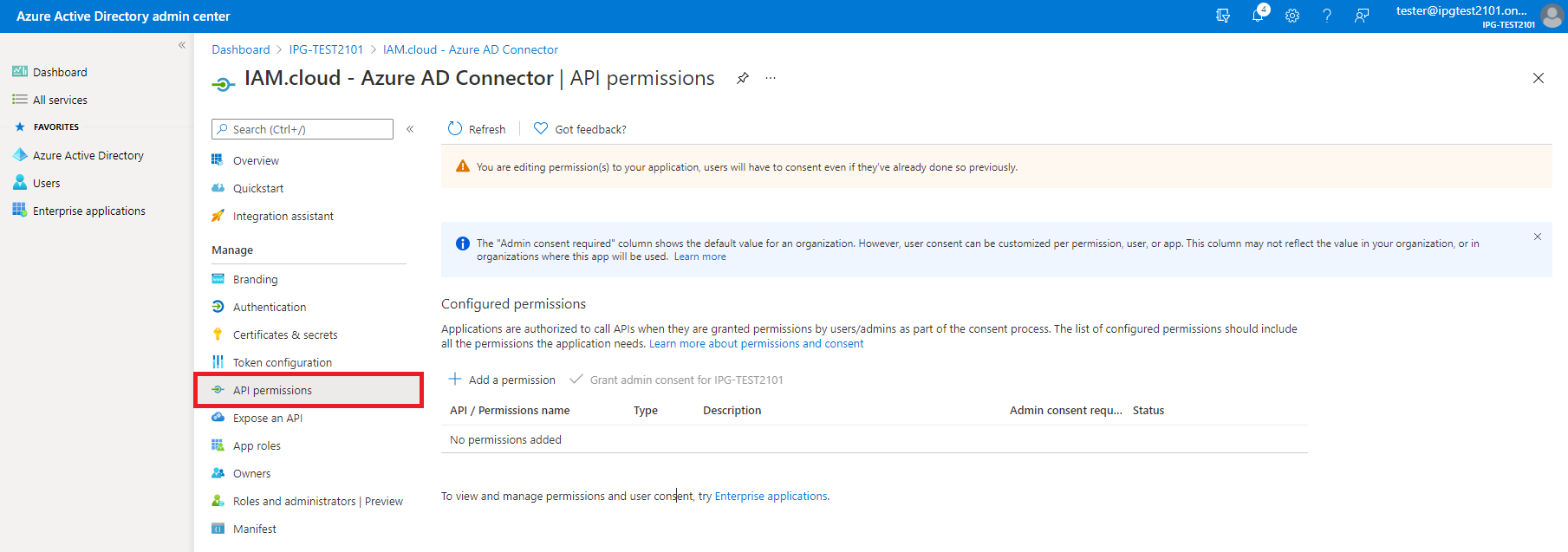
By clicking “Add a permission”, add the following permissions to the application by selecting “Microsoft Graph” as the API and “Delegated permissions” as the type of permissions:
Sign in and read user profile - User.Read
read and write access to user profile - User.ReadWrite
read and write all users' full profile - User.ReadWrite.All
read and write all groups - Group.ReadWrite.All
read and write directory data - Directory.ReadWrite.All
access directory as the signed in user - Directory.AccessAsUser.All
sign users in - openid
Some of these permissions require administrative consent - this needs to be granted.
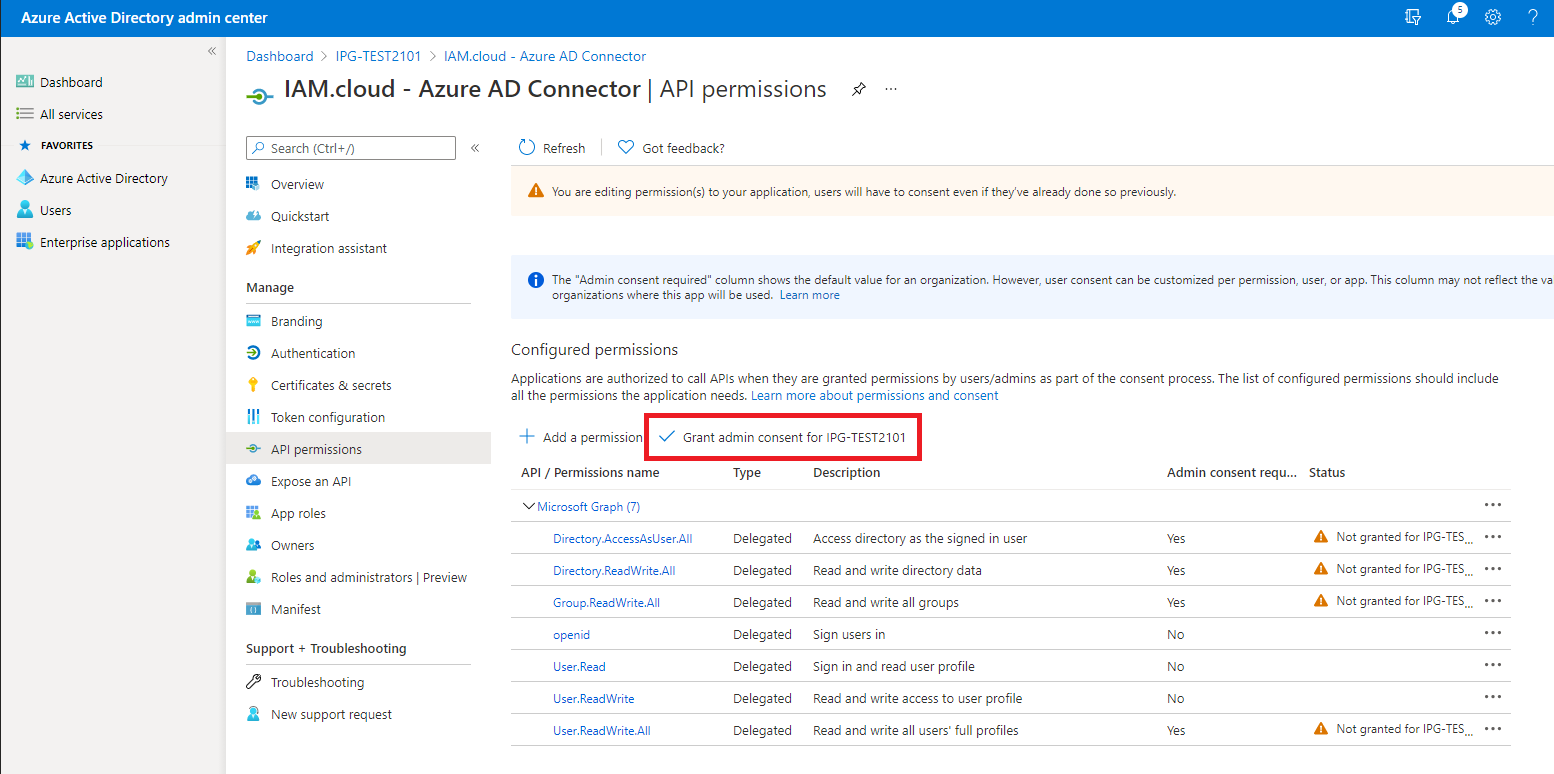
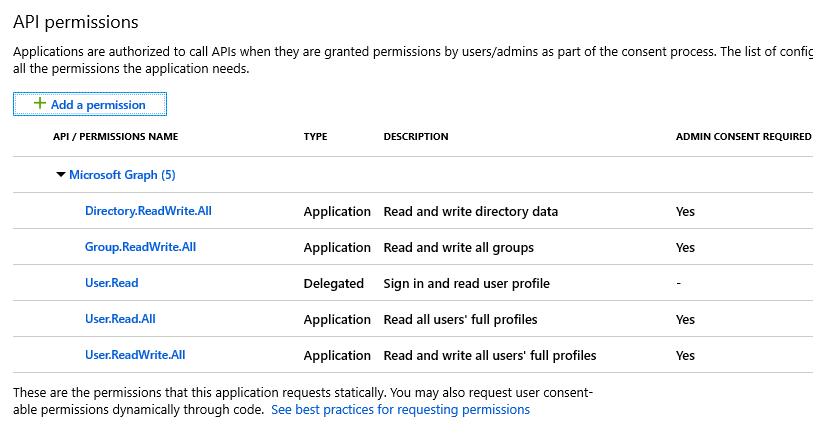
Add the following Application permissions as well:
- Application.ReadWrite.All
Directory.ReadWrite.All
Group.ReadWrite.All
User.Read.All
User.ReadWrite.All
- Policy.Read.All - (permission newly added)
- RoleManagement.ReadWrite.Directory - (permission newly added)
Some of these permissions require administrative consent - this needs to be granted.
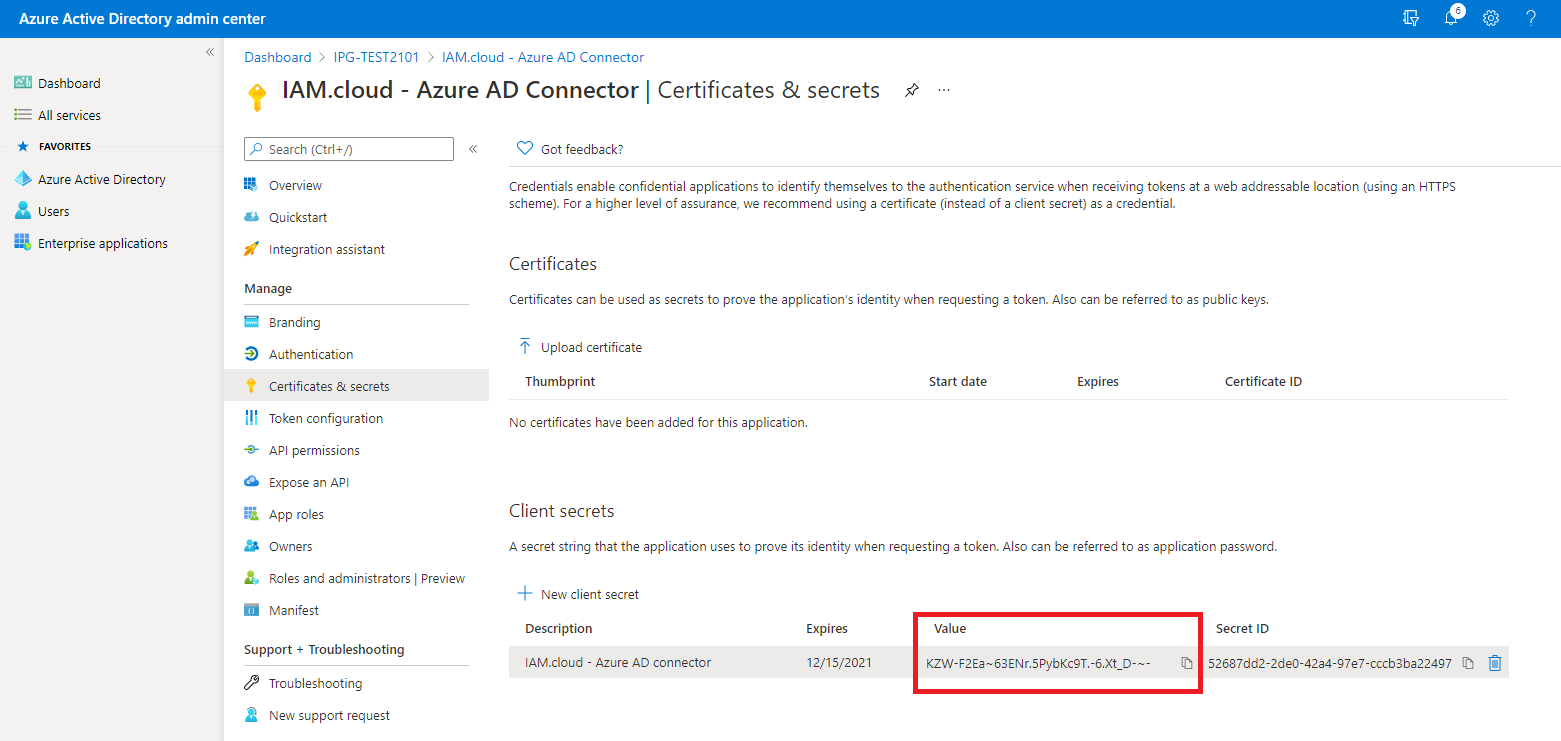
Configure the client secret using the option “Certificates & secrets” and clicking the button “New client secret”. Keep the secret value for the setup of the target system connector.
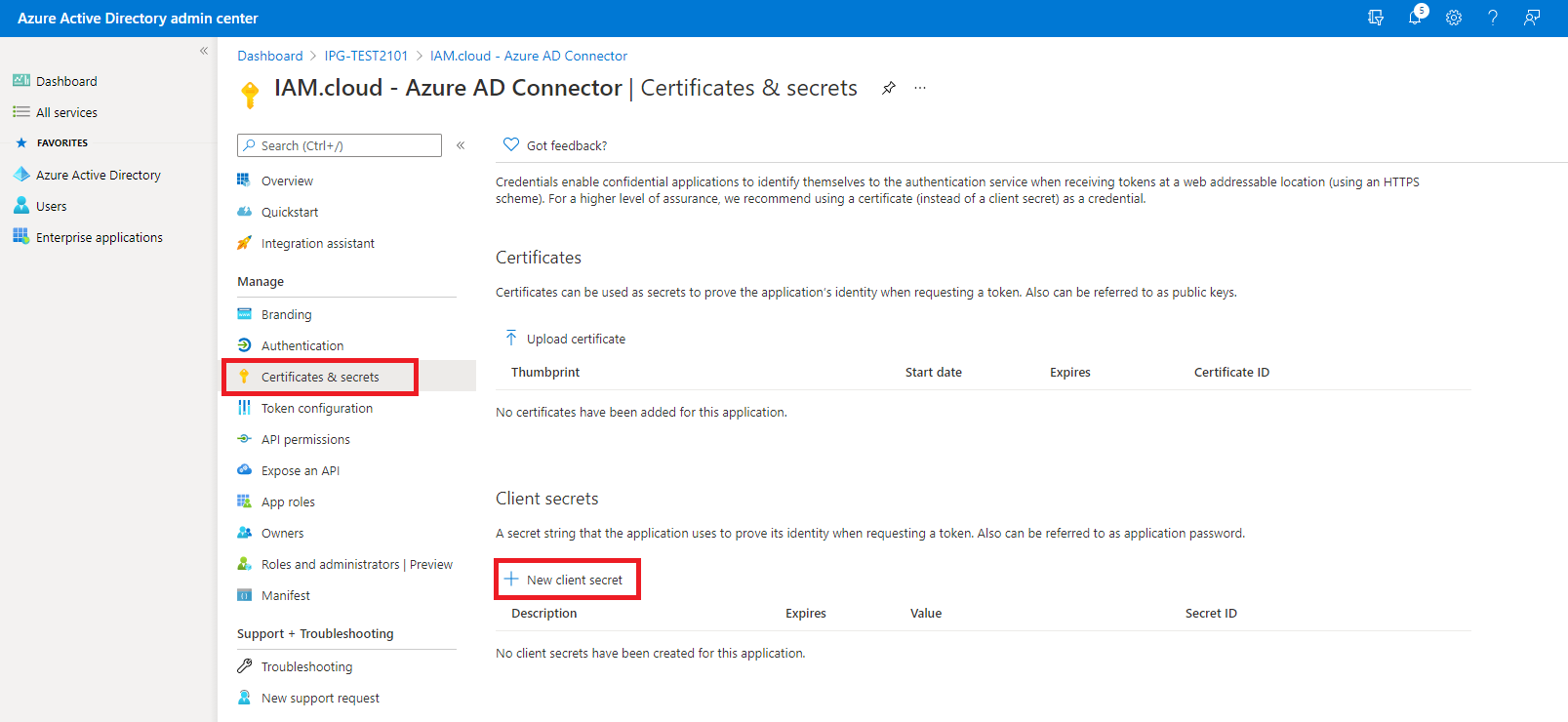
Hint: Copy the secrets value directly after creating it - it’s needed for setting up the target system connector.
Setting up the target system connector
To connect to an Azure Active Directory connect to the IAM.cloud portal with a user having the IAM.cloud application role “Global Target system configurator”. Click “Responsibilities” and “Target systems”.
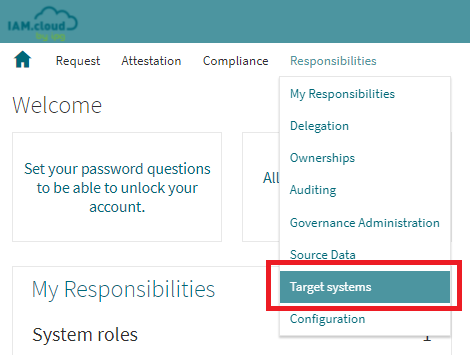
In the list of available target system connectors select the connector “Azure Active Directory“ and click the button “Setup” to create a new target system instance.

Name the target system instance, put in a description and select the IAM.cloud Gateway as the execution server.

Attribute | Description |
|---|---|
Target system instance | The name of the target system instance - this is a freetext value with no technical relevance and will be used as the display name for the target system instance only. |
Description | The description to the target system instance - this is a freetext value with no technical relevance and will be used for documentation purposes only. |
Execution server | The server that will be executing the target system connectivity tasks. This has to be the IAM.cloud cloud Gateway in order to connect to the Azure Active Directory. |
After entering the target system instance attributes, click “Save” to enable the technical configuration of the target system connector.
Fill in the technical attributes for the target system connector and click “Save”.
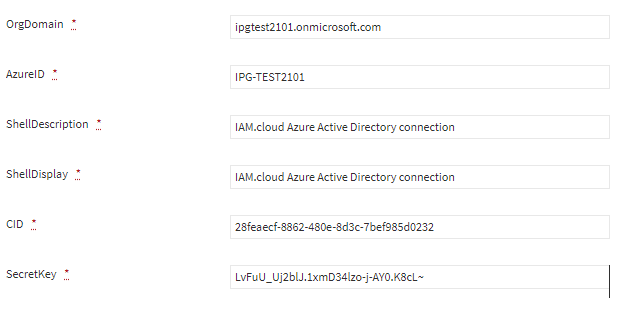
Attribute | Description |
|---|---|
ShellDisplay | The value in the attribute ShellDisplay will be used as the name of the technical connectivity setup. |
ShellDescription | The value in the attribute ShellDescription will be used for documentation purposes for the technical connectivity setup. |
OrgDomain | Azure Active Directory org domain name 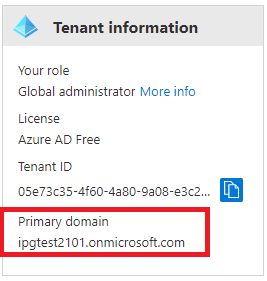 |
AzureID | The ID of the Azure tenant 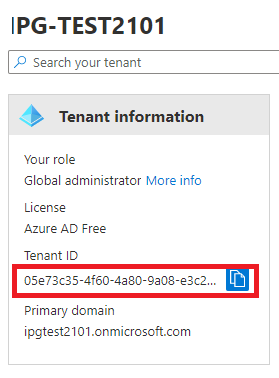 |
CID | Client-ID / Application ID of the created enterprise application |
SecretKey | The secret key that was created during the setup of the enterprise application |
AADPasswordPolicy | This attributes represents the password policy that will be applied while creating new user accounts by IAM.cloud. The default password policy is called “Azure Active Directory password policy”. If customers wish to leverage customer specific password policies, reach out to your IPG account representative or open a service request. |
If all mandatory attribute values are filled in and the configuration is saved, the button “Rollout” will be enabled. Click “Rollout” to connect the Azure Active Directory to IAM.cloud.
Related articles
-
Page:
-
Page:
-
Page:
-
Page:
-
Page: